
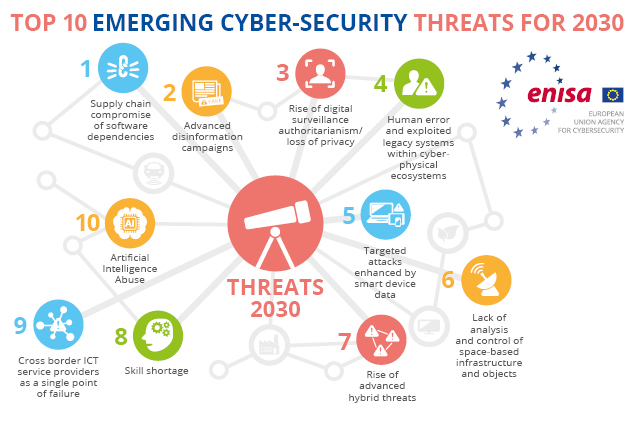
Imagine our world as a vast digital cityscape, bustling with information
and connections. Within this vibrant landscape, nestled among towering server banks and shimmering
data streams, lurks a constant threat: cybersecurity vulnerabilities. Understanding why
cybersecurity matters isn't just about securing passwords or avoiding suspicious emails; it's about
safeguarding the very foundations of our digital lives – our privacy, our finances, and even our
national security.
Cybersecurity becomes crucial for safeguarding:
» Our Privacy: Protecting our personal information from
unauthorized access and misuse.
» Our Sense Of Security: Ensuring peace of mind and resilience
against online threats.
» Our Ability To Trust: Fostering trust in online platforms and
transactions, enabling secure e-commerce and communication.
In the bustling digital jungle, where information streams like a roaring
river and connections stretch across continents, a lurking danger silently prowls: cybersecurity
threats. These hidden pitfalls threaten our privacy, finances, and even national security, demanding
our attention and strategic defense. Unmasking the scale of these threats, the challenges we face,
common attacks, and persistent myths is crucial for building a resilient digital
fortress.
The Looming Shadow: A Quantitative Reality of
Threats
The statistics paint a chilling picture of the digital
landscape:
- 22 million phishing emails, each a masterfully woven snare, slither into inboxes every single
day.
- Every 39 seconds, the digital ecosystem witnesses a malware attack, a relentless reminder of the
constant digital siege we face.
- A staggering 60% of organizations globally remain tethered to ancient systems, creating gaping
vulnerabilities like chinks in a medieval castle wall.

Navigating the Complexity: Challenges We Face
- The Human Factor: Human fallibility remains a critical
vulnerability. Weak passwords and susceptibility to phishing attacks can bypass even the most
robust technical defenses.
- Cybercrime as a Booming Industry: Gone are the days of
rogue hackers; cybercrime has morphed into a sophisticated business, with professional groups
and even nation-states wielding advanced tools and techniques.
- An Ever-Shifting Landscape: Cybercriminals, like elusive
chameleons, adapt and innovate constantly, necessitating continuous vigilance and proactive
defense strategies.
The Faces of Danger: Common Cybersecurity Threats
To effectively defend ourselves, we must recognize the
enemy. Be wary of these prevalent threats:
- Phishing and Social Engineering: Deceptive emails, texts,
or phone calls designed to lure victims into revealing sensitive information.
- Malware: Malicious software that can steal data, disrupt
systems, or hold information hostage for ransom.
- Ransomware: A particularly heinous form of malware that
encrypts your data, demanding payment for its decryption.
- Data Breaches: Unauthorized access to sensitive
information, impacting individuals, businesses, and even governments.
Several misconceptions cloud our understanding of
cybersecurity:
| MYTH |
FACT |
| Only large corporations are targets. |
Small businesses and individuals are increasingly targeted for
their valuable data or to gain access to larger networks. |
| Antivirus software is enough. |
A layered approach incorporating firewalls, data encryption,
and user awareness training is essential. |
| You'll never be a victim. |
Everyone is at risk, and vigilance is key to minimizing your
vulnerability. |
| Cybersecurity is solely the IT department's responsibility. |
All employees play a role in keeping a company cybersafe. |
| If Wi-Fi has a password it's secure. |
All public Wi-Fi can be compromised, even with a password. |
| You'll know right away if your computer is infected. |
Modern malware is stealthy and hard to detect. |
| Personal devices don't need to be secured at work. |
All smart devices, including wearables, can compromise a network's system. |
| Complete cybersecurity can be achieved. |
Cyber preparedness is ongoing, with new threats emerging every day. |
Understanding the scale, challenges, and misconceptions
surrounding cybersecurity is just the first step. We must actively build a safer digital future for
ourselves and future generations. Here's how you can contribute:
- Adopt Robust Security Practices: Use strong passwords,
enable two-factor authentication, and update software regularly.
- Be Wary of Online Scams and Phishing Attempts: Think
before you click, scrutinize email senders, and never share sensitive information through
unsolicited channels.
- Advocate For Strong Cybersecurity Measures: Encourage
businesses and organizations to prioritize cybersecurity and invest in robust protective
measures.
- Stay Informed and Update Your Knowledge: Keep yourself
updated about the latest cybersecurity threats and trends through reliable sources.
Several factors fuel this alarming trend:
- Increased Reliance on Technology: As our lives and
businesses migrate online, the attack surface for cybercriminals expands exponentially. Every
click, every transaction, leaves a digital footprint, a potential entry point for malicious
actors.
- Financial Rewards: Cybercrime has become a lucrative
industry, driven by the potential for massive financial gains. Stolen data, ransomware attacks,
and even virtual currencies offer immense profits, motivating individuals and organized crime
alike.
- Technological Advancements: Cybercriminals leverage the
latest tools and techniques, developing increasingly sophisticated malware, phishing scams, and
hacking methods. With each technological leap, they outpace outdated defenses, creating new
vulnerabilities.
- Evolving Regulatory Landscape: While regulations tighten
in some areas, the global nature of cyberspace poses challenges. Cybercriminals exploit weaker
regulatory environments, making it difficult to track them down and bring them to justice.
The Ripple Effect: Impacting Lives and Economies
The consequences of cybercrime are far-reaching, impacting
individuals, businesses, and even national security:
- Financial Losses: Businesses can suffer crippling
financial losses from data breaches, ransomware attacks, and operational disruptions. In 2021
alone, cybercrime cost global businesses an estimated $6 trillion.
- Identity Theft: Compromised personal information can lead
to identity theft, impacting credit scores, financial well-being, and even access to essential
services.
- Reputational Damage: Data breaches and cyberattacks can
severely erode public trust and damage an organization's reputation, taking years to rebuild.
- National Security Threats: Cyberattacks on critical
infrastructure, power grids, and government systems can disrupt essential services and endanger
national security.

The statistics paint a grim picture, but they cannot fully
capture the human cost of cybercrime. The stress, anxiety, and emotional toll of identity theft,
financial loss, and privacy violations can be devastating. Cybercrime thrives in the shadows,
leaving invisible scars on individuals and communities.
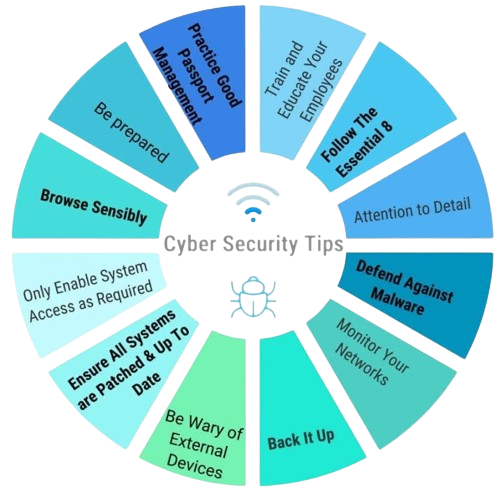
Building a Digital Defense: How to Stay Safe
In the face of this growing threat, vigilance and proactive
measures are essential:
- Practice good cyber hygiene: Use strong passwords, enable
two-factor authentication, and update software regularly.
- Be wary of online scams: Think before you click,
scrutinize email senders, and never share sensitive information through unsolicited channels.
- Protect your devices: Install antivirus and anti-malware
software, and be cautious about downloading applications from unknown sources.
- Stay informed: Educating yourself about the latest cyber
threats and trends is crucial for staying ahead of the curve.
The Cyber Two-Sided Coin: Advantages and Risks of
Building a Digital Fortress
In the digital age, where data flows like a boundless river
and connections bridge continents, cybersecurity has become the cornerstone of our online existence.
It's more than just firewalls and passwords; it's the invisible shield that protects our privacy,
finances, and even national security. Yet, like any powerful tool, cybersecurity presents a
two-sided coin, offering advantages and disadvantages that demand careful
consideration.
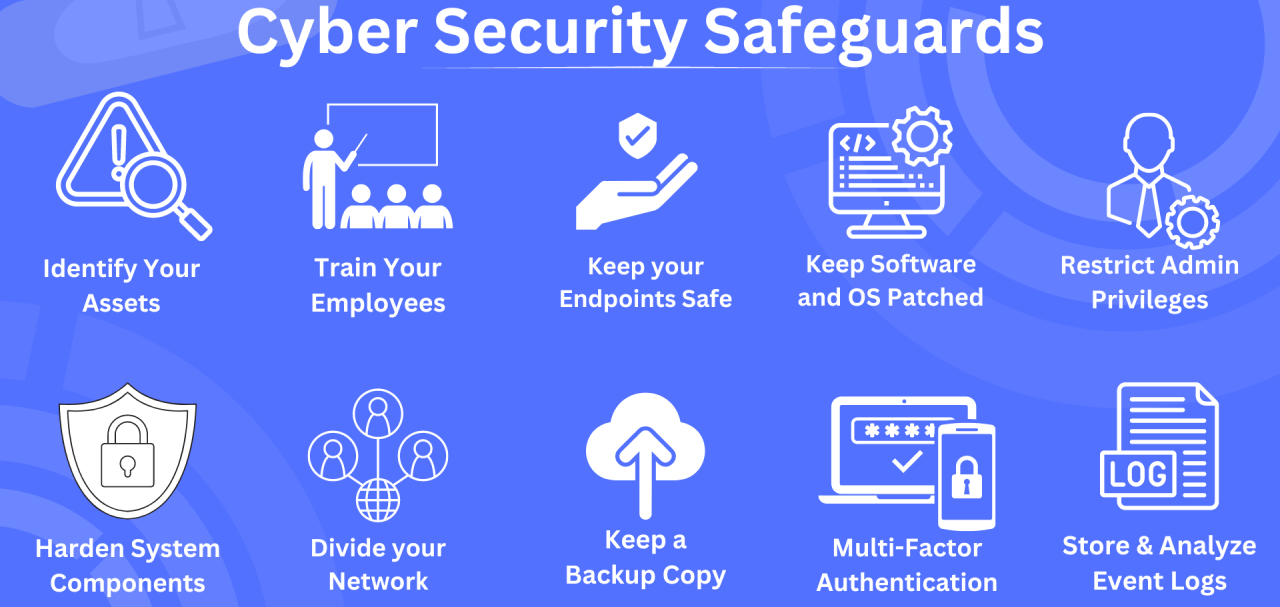
Investing in robust cybersecurity comes with undeniable advantages:
- Enhanced Security: A layered approach incorporating
firewalls, data encryption, and user awareness training significantly reduces the risk of
cyberattacks and data breaches.
- Financial Protection: Businesses safeguard sensitive
financial information and operational systems from ransomware attacks and financial fraud,
minimizing potential losses.
- Reputational Resilience: Data breaches and cyberattacks
can erode public trust and damage an organization's reputation. Strong cybersecurity mitigates
these risks, fostering trust and confidence.
- Increased Productivity: Secure systems and networks
translate to fewer disruptions and downtime, enhancing overall productivity and operational
efficiency.
- A Global Shield: Strong national cybersecurity postures
protect critical infrastructure and sensitive government data, contributing to global stability
and international cooperation.
The Downsides: Weighing the Costs and Challenges
In the digital age, where data flows like a boundless river
and connections bridge continents, cybersecurity has become the cornerstone of our online existence.
It's more than just firewalls and passwords; it's the invisible shield that protects our privacy,
finances, and even national security. Yet, like any powerful tool, cybersecurity presents a
two-sided coin, offering advantages and disadvantages that demand careful
consideration.
Investing in robust cybersecurity comes with undeniable advantages:
- Initial Investment: A layered approach incorporating
firewalls, data encryption, and user awareness training significantly reduces the risk of
cyberattacks and data breaches.
- Potential Disruption: Businesses safeguard sensitive
financial information and operational systems from ransomware attacks and financial fraud,
minimizing potential losses.
- Constant Vigilance: The ever-evolving landscape of cyber
threats necessitates continuous monitoring, updates, and adaptation, demanding ongoing resource
allocation.
- Balancing Security and Convenience: Achieving the optimal
balance between robust security and user-friendliness can be challenging, requiring careful
design and user education.
- Human Factor Vulnerability: No system is foolproof. User
errors and social engineering scams can bypass even the most advanced technical defenses.
Real-World Consequences: The Scars of Cybercrime
To truly understand the stakes, consider these stark
examples of cyberattacks and their consequences:
- Marriott International (2018): Hackers accessed data of
over 500 million guests, resulting in a hefty $123 million settlement and lasting reputational
damage.
- Equifax (2017): A massive data breach exposed the personal
information of over 147 million Americans, impacting credit scores and financial well-being.
- Wannacry ransomware attack (2017): This global attack
crippled critical infrastructure in hospitals, banks, and government agencies, causing billions
of dollars in damage and disruption.
- Yahoo (2013-2014): Hackers stole data from over 3 billion
user accounts, raising serious concerns about user privacy and eroding trust in the platform.
- Target (2013): Hackers accessed credit card information of
over 40 million customers, resulting in financial losses and a tarnished reputation.

Is Your Business Vulnerable? Recognizing
the Risk...
Every organization, regardless of size or industry, is a
potential target. Factors like:
- Storing Sensitive Data: Businesses holding customer
information, financial records, or intellectual property are prime targets.
- Outdated Systems: Vulnerabilities in legacy systems offer
easy entry points for cybercriminals.
- Lack Of Cybersecurity Awareness: Untrained employees are
susceptible to phishing attacks and social engineering scams.
By assessing these factors and conducting regular security
audits, businesses can identify vulnerabilities and proactively mitigate potential risks.
The Choice is Ours: Building a Secure Digital
Future
The decision to prioritize cybersecurity is not simply a
financial calculation; it's a strategic investment in our collective digital future. By balancing
the advantages and disadvantages, implementing robust security measures, and promoting user
awareness, we can navigate the digital landscape with confidence, harnessing its potential while
mitigating the risks. Let's work together to build a secure and resilient digital world where
innovation thrives alongside safety and trust.
Remember, cybersecurity is not an expense;
it's an investment in our digital well-being. Choose to build your digital fortress, brick by
digital brick, and make the internet a safer place for everyone.
Credits: Ms. Swati Jain
|
19 Shares
|
March 12, 2024
|









